It was a rush to get out the door before a long-awaited holiday - or at least that’s what I’ve told myself. In the end there’s no excuse - I’m a seasoned computer user with over two decades of experience and I’ve run Windows and Macs and been infected with many viruses and more recently malware during that time. Sometimes I feel a bit stupid when I recall contracting malware by my own hand and certainly back in the days when I was running Windows XP as my primary operating system, there were plenty of bad things out there to disrupt my otherwise nice clean computing machine. Then I switched to Macs, lured by their reliability, simplicity and the “fact” that they didn’t get viruses.
Of course, I knew then as I do now that Macs are still vulnerable to attack, but with keeping my Mac up to date with software updates from Apple and not just clicking on anything that just looked out of place asking for my username and password, I ran my Macs without an anti-virus scanner for years but enough of the flashbacks to yesteryear.
Today I returned from my holiday, having read all about the issues when away on my iPad the very first thing I did was run a few command line entries in Terminal. To my initial joy, nothing showed up - despite my recollection of running a Flash Installer just prior to leaving on my holiday. I proceeded to then download FlashbackChecker and ran it - also coming up clean. I then proceeded to one last website to ensure that I was clean and checked the machine UUID in its database of known accessed computers to find the following:
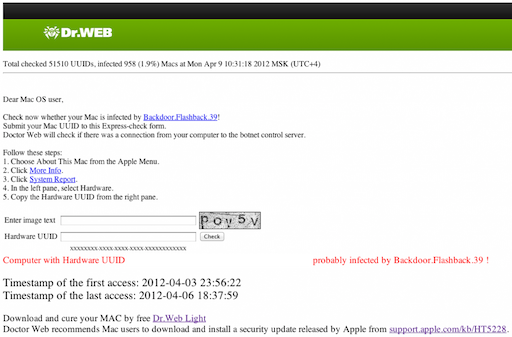
Oh dear. To be sure it wasn’t just trying to get my money or something similar, I tried on the other Mac in the household with this result:
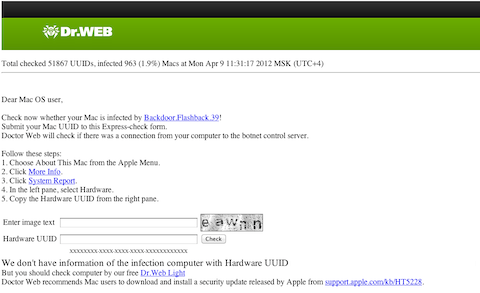
Indeed my first Mac had been infected, however its last check in was days prior and it ran the whole time I was away. What I did do during my holiday (as I am a geek after all) was to use LogMeIn to access my Mac from my iPad and ran my Software Updates which installed java Java update 002.
Looking for more answers as the plot thickened I proceeded to download ClamXAV the freeware anti-virus scanner for the Mac and scanned my boot volume and it returned this result:

I proceeded to delete the file and upon a reboot was able to empty the trash. A rescan of my Mac came up clean.
So what happened? The facts seemed to suggest that I was infected but the Apple update removed or at least disabled the infection. Alternatively the pre-installer detected Xcode on my system and self-deleted. In either case a remnant of the infection was the .null file that I was able to remove without too much trouble. Nothing on my Mac was damaged and everything is backed up and whilst my Mac may be been used as a part of a BotNet for a brief period, no harm was done: so far as I know.
The Mac is a very secure operating system, however it’s not virus/malware proof as this illustrates. The root of the problem seems to be that the Apple-authored Java runtime had a known issue that was patched already by Sun Microsystems (the originators of Java that maintain their own runtime for other operating systems) but Apple had lagged behind some six weeks before it released a patch for the same issue. Flashback had been around for months previously (back in September, 2011 it’s first incarnation was first detected) however it was not until recently that a version requiring no username or password was in the wild and the unpatched systems were waiting to be taken.
Many sites have indicated that the best approach is to disable Java. Certainly this will plug this specific hole, but it won’t fix anything else. People running Lion don’t even have Java installed by default it must be separately downloaded from Apple and this would only occur IF the user needed to use it for some reason. Disabling it would seem counter-productive therefore since the user clearly needed it at some point and will likely need it again - if not even regularly.
The simplest take-aways from this experience are two things: 1) A message to Apple to take malware threats more seriously and work faster to patch issues they become aware of and 2) users should have some basic AV Scanner - not running in the background necessarily but at least scheduled to do a weekly scan just in case.
It’s worth mentioning that ClamXAV found two other spoofing emails in my history but that’s all - neither of which sucked me into clicking their embedded links. The point is that for an installation that’s as old as Lion (approaching a year shortly) this was the only real issue found.
In short, I placed too much trust in OSX and the Mac. Lesson learned: the hackers are watching.